A pretty shocking thing came to light this evening – Lenovo is installing adware that uses a “man-in-the-middle” attack to break secure connections on affected laptops in order to access sensitive data and inject advertising. As if that wasn’t bad enough, they installed a weak certificate into the system in a way that means affected users cannot trust any secure connections they make – TO ANY SITE.
We trust our hardware manufacturers to build products that are secure. In this current climate of rising cybercrime, if you can’t trust your hardware manufacturer, you are in a very difficult position. That manufacturer has a huge role to play in keeping you safe – from releasing patches to update software when vulnerabilities are found to behaving in a responsible manner with the data the collect and the privileged access they have to your hardware.
When bad guys are able to get into the supply chain and install malware, it is devastating. Often users find themselves with equipment that is compromised and are unable to do anything about it. When malware is installed with the access a manufacturer has, it buries itself deep inside the system – often with a level of access that takes it beyond the reach of antivirus or other countermeasures. This is why it is all the more disappointing – and shocking – to find a manufacturer doing this to its customers voluntarily.
Lenovo has partnered with a company called Superfish to install advertising software on it’s customer’s laptops. Under normal circumstances, this would not be cause for concern. However, Superfish’s software has quite a reputation. It is a notorious piece of “adware”, malicious advertising software. A quick search on Google reveals numerous links for pages containing everything from software to remove Superfish to consumers complaining about the presence of this malicious advertising tool.
Superfish Features:
- Hijacks legitimate connections.
- Monitors user activity.
- Collects personal information and uploads it to it’s servers
- Injects advertising in legitimate pages.
- Displays popups with advertising software
- Uses man-in-the-middle attack techniques to crack open secure connections.
- Presents users with its own fake certificate instead of the legitimate site’s certificate.
This presents a security nightmare for affected consumers.
- Superfish replaces legitimate site certificates with its own in order to compromise the connections so it can inject its adverts. This means that anyone affected by this adware cannot trust any secure connections they make.
- Users will not be notified if the legitimate site’s certificate has been tampered with, has expired or is bogus. In fact, they now have to rely on Superfish to perform that check for them. Which it does not appear to do.
- Because Superfish uses the same certificate for every site it would be easy for another hostile actor to leverage this and further compromise the user’s connections.
- Superfish uses a deprecated SHA1 certificate. SHA1 has been replaced by SHA-256 because attacks against SHA1 are now feasible with ordinary computing hardware. This is insult on top of injury. Not only are they compromising people’s SSL connections but they are doing it in the most cavalier, insecure way possible.
- Even worse, they use crackable 1024-bit RSA!
- The user has to trust that this software which has compromised their secure connections is not tampering with the content, or stealing sensitive data such as usernames and passwords.
- If this software or any of its control infrastructure is compromised, an attacker would have complete and unrestricted access to affected customers banking sites, personal data and private messages.
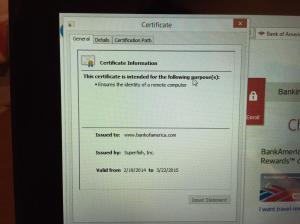
Below is a photo showing Superfish on an affected laptop presenting a fake certificate instead of the legitimate “Bank of America” certificate. As you can see the user is presented with the fake Superfish certificate instead of the legitimate BoA certificate.
The only way a user would know this has happened is if they check the certificate’s details. Something most ordinary users are unlikely to do to a certificate which to all other appearances is valid and secure.
As mentioned above, the certificate used by Superfish is a deprecated SHA1 certificate that uses 1024-bit RSA. This is particularly obnoxious because they have installed into the system certificates as an unrestricted trusted root certificate. To put it into context, they gave it the same level of trust and authority as Microsoft’s own root certificate. Users affected by this can go to any site on the internet, and so long as it presents this certificate, they will be fooled into thinking they have a secure connection. Since this certificate uses SHA1 it is feasible that an attacker could break it and hijack it. This means an attacker could create a bogus certificate that every one of these users would trust.
This is unbelievably ignorant and reckless of them. Its quite possibly the single worst thing I have seen a manufacturer do to its customer base. At this point I would consider every single one of these affected laptops to be potentially compromised and would reinstall them from scratch.
Lenovo’s response? Typical of companies caught with their hand in the cookie jar, they try to play it down while at the same time saying they have disabled it until it can be “fixed”:
However, it’s hard to see how they could “fix” this software. It’s core functionality undermines the security of SSL rendering the last decade or so of work making the web secure completely irrelevant.
UPDATE: –
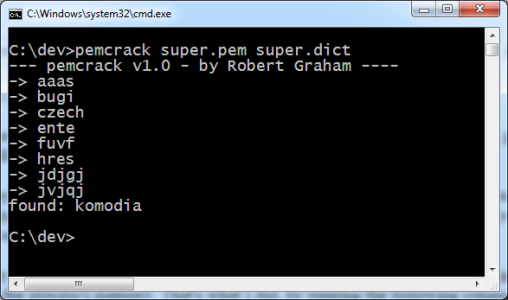
It’s not often that things like this actually get worse. This one has. So, because the man-in-the-middle happens locally, it’s clear that the private key has to be bundled with the software. This is because in order to sign sites on the fly, the software has to do that with the private key.
This is really bad practice. What makes it even worse is that they used a simple dictionary word as the password for the key. After a little reverse engineering, it is possible to extract that key and crack the password. Armed with the private key and its password, you can now sign websites and even software in a way that any affected Lenovo user will trust. What’s worse is you can do it under any fake name that you like. Want to sign a virus so that it looks like legitimate Microsoft software? Go ahead: this will let you do exactly that. Want to set up a fake banking site and pretend to be HSBC? Yup, you can do that too.
Who needs to crack SHA1 or factor RSA-1024 if all you need to do is extract the private key? Game Over.
What was the password they used? Komodia. Both a ridiculously easy dictionary word and the name of a well known manufacturer of SSL products. What’s the betting that they are behind this, and that their own SSL proxy products are designed in a similarly terrifying way?
Read more about the reverse engineering of Superfish on Errata Rob’s Blog –
http://blog.erratasec.com/2015/02/extracting-superfish-certificate.html#.VOY1QCmJndk
HOW TO CHECK IF YOU ARE AFFECTED:
My colleague Filippio – @FiloSottile has written a detector for superfish affected laptops. To test if you are affected simply click on the URL below:
WHAT TO DO IF YOU ARE AFFECTED:
Lenovo has published instructions for removing the app:
I have checked them and they are sound BUT they do not provide instructions for removing the malicious certificate in the system certificate store.
To remove the certificate (which is the worst part) follow these instructions:
- Go to Control Panel and search for ‘certificates’.
- You’ll find yourself in Administrative Tools.
- Select “Manage computer certificates” ,
- click on the folder labeled Trusted Root Certification Authorities
- Click on Certificates.
- Find the one labelled “Superfish Inc”, right-click and chose to delete it
HT to @semenko @kennwhite @fugueish on twitter for the screenshots!




Is this only on Laptops or Lenovo PCs as well?
As far as I am concerned any recent Lenovo device should be tested to be safe.
bastards
Hi, thank you for your article. My question now is, if I am “stuck” with a Lenovo laptop, what can I do to fix this problem?
Thanks
Joel
Thats a tricky question. Ill add some details to my blog.
The quick answer however is find a superfish remover app online and run it to remove the adware. Then find and delete the superfish key in your certificate store.
I would throw away the computer or install a whole new operating system and applications
I have just run a test on my wife’s and daughters new Lenovo Tabs. Both are infected
F
U
C
K
L
E
N
O
V
O
Reblogged this on Benjamin Fisher-Merritt (author) and commented:
Just something for any of my followers who might have Lenovo laptops to consider…
Here’s a good site to check if you’re vulnerable:
https://canibesuperphished.com
That test is ok but it isn’t conclusive – what it does is present a bad certificate, if the certificate comes up as ok then you might be affected.
Use the one my colleague put up instead. His test actually uses the superfish certificate to check:
https://filippo.io/Badfish/
Our company leases a fleet of about five thousand Lenovo laptops, and has been loyal to the brand since it was the IBM ThinkPad.
We’re a bank. There is an arguable case for ending this relationship *now* because a supplier with that attitude to customer security could do anything – anything at all, and many, many things that are equally exploitative, dishonest and dangerous – and there is no reason whatsoever to believe their assurances to the contrary.
Reblogged this on Zombie Code Kill.
The removal instructions are inadequate for Firefox users, as Komodia (the SDK used by Superfish) also inserts the root CA cert in the NSS store.
You need to also proceed to “tools -> options -> certificates -> authorities” in Firefox and delete the Superfish CA.
Thanks for pointing that out!
This whole thing is disgusting, so please don’t think I’m sticking up for Lenovo here, but (not having the equipment to test) I’m puzzled about the issues involving their local root certificate.
Surely it is only accepted by the local browsers when they talk to the superfish program, and NOT the Superfish program as it talks to the outside world, therefore making concerns over thr cerificate key strength/password etc. moot?
Extending on this, interestingly it would bbecome a problem when the software is removed if the client-installed root certificate is left behind?
cheers, Jamie
The certificate is used to fool the users that they are connecting to a trusted site and getting a secure connection. When you connect to yourbank, the superfish software talks to yourbank instead of you. It negotiates the connection and establishes SSL between it and yourbank. Then the superfish software presents a fake certificate that claims to be yourbank back to your browser. Your browser trusts it because of the certificate in the root store. So you carry on and do your banking thinking you have a secure connection when you dont.
The problems dont just stop there. Because this certificate is so weak, anyone can take it’s private key use the password and sign anything from fake certificates to viruses or malware and your PC will trust it because it is signed by a trusted certificate.
All those controls to stop malware by only allowing signed programs? now worthless on one of these laptops. I cannot understate how evil this is.
Hi! Thanks for your reply!
I understand that, but maybe I didn’t explain my point clearly (which was made before we knew that the way the superfish program checks certificates was flawed anyway, making my point moot)
What I was saying is that with superfish installed, the weak certificate is used for the https link between the browser and the local superfish program. As long as the superfish program itself doesn’t trust the same weak certificate, then it’s weakness is irrelevent, as it is only exposed Clientsuperfish . Whether or not superfish does accept it’s own weak certificate when connecting externally was not mentioned, thus I was just saying that it’s stated knock-on effects were being assumed.
Following from this, I pointed out that if the dodgy certificate is insulated from the world in this way, then its risks are only exposed if superfish is removed, but the weak certificate isn’t!
I totally take your secong point though – I was thinkging only about SSL/TLS cojnections, ehich superfish intercepts.
I hadn’t even thought about software signing etc.
cheers!
jamie
I guess the lesson is always format and clean install a new Windows machine.
Is this vulnerability baked in at the hardware or firmware level, or only in Lenovo’s default factory Windows installation? How far down does the rabbit hole go? Has anyone attempted a fresh non-factory install of Windows, or Linux on a Lenovo machine, and reproduced the same vulnerability?
Its a software package that’s installed as part of Lenovo’s OEM software customization to windows.
It can be removed like any other package and a fresh install of windows also removes it so long as you don’t restore the lenovo software afterwards 😉
Hi, thanks for the article.
We image all our Lenovos so I assume this isn’t a threat. Still, very troubling.
Never assume anything.
Unless you’re purchasing consumer products for your business, you’re likely ok. This is for IdeaPad type stuff, not the ThinkPad line.
actually komodia in greek means “comedy”. Pure comedy
I have to say I get in a lot of new laptops from the likes of Acer/Asus/Lenovo/Toshiba/HP etc. and the amount of junkware they load these poor machines up with just creates a nightmare for the customer.
You end up with a laptop experience akin to buying a clown car.
A lot of the junkware stops you actually being able to use the damn laptop until you’ve finished registering/installing it all.
Doesn’t reflect well on the manufacturer or Microsoft’s Windows. In fact I get a lot of people moaning about the junkware hassles being a good enough reason to move over to a Mac. But if you just install the junk the laptop works smoothly.
Junkware needs to come to an end. People will pay more for what they feel is a good user experience, in fact several hundred dollars more…just ask Apple.
Lists of products from/using Komodia are appearing, probably everything to do with that company has this, I would guess.
Wasn’t there a firewall called Komodo a while back? I see it’s Comodo now, but they are in a business that is right up this same alley. Though no Israel office listed, I sure hope they are not affiliated with Komodia, but it’s hard to tell.
Somebody on Twitter said that this is the kind of sleazy trick that the US government pulls, and you wouldn’t expect it from a reputable Chinese business.
At least they were nice about using the standard Windows program installation system for installing their malware, rather than hiding it deeply like professional malware software.