 So, as people have started turning over stones, looking to see how common these Komodia certificates are, some surprising (and depressing) things are beginning to surface.
So, as people have started turning over stones, looking to see how common these Komodia certificates are, some surprising (and depressing) things are beginning to surface.
- It does appear that Komodia is behind this.
- It appears that Komodia uses the same framework for many, many products. Here’s some that have been found so far:
- Komodia’s “Keep My Family Secure” parental control software.
- Qustodio’s parental control software
- Kurupira Webfilter
- Staffcop (version 5.6 and 5.8)
- Easy hide IP Classic
- Lavasoft Ad-aware Web Companion
- Hide-my-ip (note: this package does not appear to utilize the SSL MITM, and the certificate is slightly different from the one found in other packages however it still utilizes an unrestricted root certificate with a simple plaintext password.
- The password is always “Komodia”
- The certificates are always weak; the private key is always bundled with them (of course it is).
I think that at this point it is safe to assume that any SSL interception product sold by Komodia or based on the Komodia SDK is going to be using the same method.
What does this mean? Well, this means that those dodgy certificates aren’t limited to Lenovo laptops sold over a specific date range. It means that anyone who has come into contact with a Komodia product, or who has had some sort of Parental Control software installed on their computer should probably check to see if they are affected.
This problem is MUCH bigger than we thought it was.
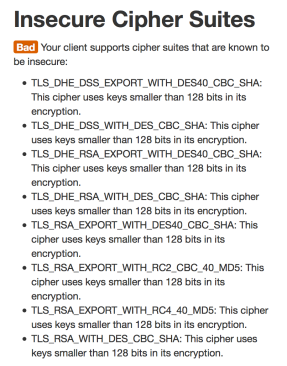
SSL Ciphers –
The next issue is that these “proxies” do not correctly implement SSL. They negotiate with the origin server on your behalf – so when you want to connect to your bank site it is this software that negotiates for you. However it does this badly. First of all it supports a range of ciphers including a number that had been deprecated years ago and others that simply should not be used – for example:
This means the Komodia proxy software may potentially establish – or be forced into establishing – a weak SSL connection using breakable ciphers. This weak connection could then be tampered with or eavesdropped on by hostile actors. the user will be completely unaware, and even if he inspects the status of his SSL connection all it would show is the strength of the connection between the browser and the Komodia software, not the connection going over the Internet.
In one move this software trashes the last decade of browser security and privacy work, and the last five years of SSL cipher management.
Certificate validation –
The next problem is that it does not appear to validate certificates properly. If a certificate fails validation, the proxy still lets it through and signs it with the Komodia certificate, but it changes the name on the certificate to “verify_fail.<whatever the original domain was>” so for example if you browse to the self signed certificate on events.ccc.de you will see a Superfish signed certificate for verify_fail.events.ccc.de. its a cheeky attempt to cause a browser warning by having the name mismatch.
However as discovered by many, if you put the correct name into the “Alternate Names” field of the certificate the software will blindly copy that name across and when it changes the primary name, the Alternate Name field will still match the expected domain and the browser will believe the certificate to be valid. Epic Fail.
More details here: https://blog.filippo.io/komodia-superfish-ssl-validation-is-broken/
If you are a parent that has installed parental control software – in particular the ones named above – I would check to see if your computer has been affected by this, as a matter of urgency –
UPDATE: @filosottile has updated his test to check for the new certificates.
If you have come into contact with any Komodia product, I would check for unrestricted private root certificates, before carefully removing them and the associated software from any system that you care about.
Thanks to @thewack0lian for pointing this out! – https://gist.github.com/Wack0/17c56b77a90073be81d3
Thanks also to US CERT for additional vulnerable packages – http://www.kb.cert.org/vuls/id/529496

http://imgur.com/H8459Z3,87zOroU
Check out Lenovo trying to lie to save face, though
USA and americans should be subject to punishment customs that collect fee for compensating all the damage their spying has caused EU and the world.
U do know that lenovo is Chinese now right?
fuck off, “USA and americans” didn’t have anything to do with this crap. dickhole.
You will get a false positive, i.e. a “Yes” that should be a “No”, if you are behind a proxy, e.g. surfing from work.
Good article. One that provides technical details instead of lot of Superfish articles out there with scary messages.
If I understand correctly, Lenovo is installing a https proxy to intercept traffic (vs common proxies you find in enterprises that use http CONNECT verb to proxy https traffic). The proxy is creating self signed certs for every https site the browser is visiting, but signed by the root CA inside the proxy. The browser’s root cert store is updated with proxy’s root CA chain. But the proxy still communicates to destination over https doing usual https validations (like checking for self-signed certs vs Verisign signed ones etc).
I don’t think someone out there in the wild can decrypt data even if they have root CA private key as the proxy to destination site is https session which is protected by destination site’s private/public key pair. I saw articles claiming that they could decrypt https traffic if they are at a Cafe by having the root CA. But how?
The https traffic that gets affected by this proxy is the one from browser to localhost:proxy port. It beats me how someone outside the box can sniff that traffic.
Am I missing something here?
But someone out there can create a site that looks like say bankofamerica.com site with self signed cert signed by above root CA and start a phishing attack. If a customer with the Superfish software press that link and go to that site, the browser won’t warn that it is a phishing site.
This is far fetched and the impact is lot less than what most of the Superfish articles are portraying. Neverthless it is a bad business decision by Lenovo to install something like this at factory. I bet they will have a challenge selling into enterprises with the -ve press that this caused.
Your understading is correct to an extent.
The proxy is not using “self signed certs” in the classical sense. The certificate that Superfish and the Komodia SSL redirector based products use is an unrestricted private root certificate.
What that means is that when anything is signed using the private key for this certificate it has the same amount of validity for these machines as a certificate signed by say Verisign or Microsoft.
Theres a few problems associated with this.
1. Certificate pinning no longer works for these machines. Because this certificate will get checked before any other certificate it will always be the first certificate used in Cert pinning.
2. Because the badly implemented SSL software suports a bunch of extremely weak ciphers an affected user could end up accidentally (or deliberately because of an attack) establishing an easy to break SSL session. Furthermore because everything is being signed by this bogus root CA, the user will be blissfully unaware.
3. Any attacker with the private key can bypass / hijack the microsoft code signing restrictions. It would be easy for an attacker to sign his malware or bogus updates with a key that identifies itself as microsoft and is completely trusted. A user would see nothing out of the ordinary and similarly most automated patching programs would probably be unable to tell the difference either. they would just see a valid certificate with the right name.
4. An attacker with this certificate can make fake certificates for ANY site on the internet and any affected user visiting them would be told by his browser that everything is ok. This is not theoretical. I have tested it and it is trivial to implement.
5. Likewise a phisher can use this to generate certificates to sign email messages. Those emails when received would look like the genuine article and the client would say that its secure and that the certificate is valid. This again leads to an easy attack – send out a few million of these. They look bogus to anyone without Komodia or superfish certs but look completely genuine to folks with them. If that is even only 5% of users received, out of 1 million emails that is still 50,000 compromised machines.
There are many more ways that this can be exploited. However we do have one thing going for us – one of the missing pieces of the puzzle is that right now it is not easy to identify passively who is affected. This makes it hard for bad guys to selectively target victims. However I would not count on this remaining the case for long.
This is why it is good that MS and various AV companies were so quick to add signatures for this adware and its certificates to their kill list.
Reblogged this on Filewatcher.