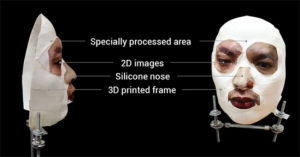
FaceID keeps on getting more and more interesting. According to Vietnamese Security firm Bkav, they were able to unlock the device using a 3D printed mask, hand made prosthetic nose, and 2D printed eyes. This seems unlikely, especially given what Apple has said previously about testing they did to secure FaceID.
What seems more likely is that Bkav were able to “weaken” the Neural Engine’s model by training it against the mask, essentially poisoning it and creating a backdoor. This is a security weakness in its own right and I’ll go into more detail why a little later on in this article. However if my suspicions are correct, then this wasn’t a true break of FaceID but rather a partial break that required prior knowledge of the device’s passcode. It’s still a clever hack, and it introduces some additional questions, the biggest one being why the “liveness test” failed to detect that these were not real eyes. Even with “require attention” turned off, to be truly secure FaceID needs to be able to tell the difference between a human and an artificial construct. Accurate liveness testing is a fundamental foundation all biometric services should be built on.
What we’ve learnt so far about FaceID…..

FaceID uses an InfraRed emitter/camera to project 30,000 dots at the subjects face. This is possible to see, and record, using a DSLR with a modified IR filter, as can be seen in this rather neat video on YouTube. Using these dots, FaceID maps your face and feeds the information to its “Neural Engine”. This machine learning model essentially trains on your face and gets better and better with time.
FaceID doesn’t need your whole face to unlock your phone. Some parts of your face appear to be optional, while others appear to be mandatory. As far as I can tell, the mandatory part is based on the triangle made by your eyes and nose. This is almost certainly to reduce the false negative rate – the measure that access control systems use to judge how many people have been incorrectly refused access. If you think about it, the eyes and nose are the most static parts of your face. Everything else – hair, ears, lips, chin/beard etc – can change daily and are the most variable in different environmental conditions. Rumored production issues with the infrared parts of the phone may have also played a role. This is perfectly reasonable as the balance between false positive and false negative rates can be the difference between a viable, secure biometric system and a complete failure. However, it does significantly reduce the complexity of what an attacker needs to do. Building an accurate map of a small part of a target’s face is much easier than the whole face.
It’s possible to unlock someone’s phone by showing it to them so they glance at it. This seems to work face on, or at an angle but it does not work from the side. For me this is the most troubling weakness in the FaceID system. If all a thief has to do is get you to look their way after snatching your phone then its not a very hard attack to imagine. The best defense appears to be to keep your screen-lock time out set very low. As anyone in forensics will tell you, it’s really hard to keep something on a timer unlocked indefinitely.
 It’s also possible to poison the Neural Engine’s model. This is what I suspect the Vietnamese security researchers from Bkav cleverly did. I think this is also the primary reason behind the frequent reports of close family members unlocking phones. Their facial structure is already similar so it probably only requires a few instances of retraining to pollute the model with attributes from another person, weakening the accuracy of the model, ironically, the exact opposite of what this mechanism is supposed to do.
It’s also possible to poison the Neural Engine’s model. This is what I suspect the Vietnamese security researchers from Bkav cleverly did. I think this is also the primary reason behind the frequent reports of close family members unlocking phones. Their facial structure is already similar so it probably only requires a few instances of retraining to pollute the model with attributes from another person, weakening the accuracy of the model, ironically, the exact opposite of what this mechanism is supposed to do.

From the testing I did with Wired, it’s clear that the way a material or surface scatters infrared is critical to getting the phone to unlock. If it doesn’t behave like human skin then it won’t, and shouldn’t, register with the phone. However this may have also helped the researchers from Bkav. The 3D printed parts of the face may not have registered at all with the phone, however the position of the eyes, held by the frame, and the depth of the handmade nose would have been critical. This I suspect will be key in any future unlocks.
In Conclusion …..

As a hacker I firmly believe anything man makes, man can break. Someone will create a way to fool facial recognition, then someone will improve it and so on. The only question we should be asking is whether or not it’s secure enough. None of the attacks we have seen so far are very practical. Who sits still for 5 minutes so someone can record their face? That said, if FaceID’s own enrollment process can be completed in a few seconds, so can an attack. It still leaves this in the realm of high-end targeted attacks, so you probably don’t worry unless the men in black helicopters really are out to get you.
However, there are still four things that leave some cause for concern –
- How easy it is for someone to snatch a phone and use your face to unlock it
- The apparent failure of the liveness testing to tell printed eyes from real ones
- The amount of your face used to unlock the phone
- The flaw in the neural engine that allows the model to become polluted
Some of these are easy to fix, some are a little harder. Knowing Apple they are already working on improvements that will mitigate some of these. ……Just as they know we will be using what we know to improve our attempts to defeat it. 🙂